Installing a CloudFlare Origin CA
CloudFlare offers free certificates to secure traffic between its CDN and your website. Using this allows using Full (String) SSL/TLS.

The default installation of the Ghost blogging certificate makes use of the LetsEncrypt provided self signed certificates. Cloudflare also provide free certificates to secure data transfer between their CDN and the blog server.
LetsEncrypt grants certificates that are quite limited in time, needing to be renewed every three months. Furthermore, the version of the client installed with Ghost does not appear to support the latest version of LetsEncrypt. At least the client that was installed when I set things up, way back in version 1.21. I could do a fresh installation, but moving to CloudFlare now seems like the best option.
An advantage of using a CloudFlare provided certificate is that the expiry can be up to fifteen years, which may be longer than the lifetime of this blog.
Using a certificate from a trusted authority or a free one provided by CloudFlare will allow me to turn on Full (Strict) SSL/TLS. The difference from Full SSL is that CloudFlare will verify the certificate on each request.
Getting a Key and Certificate
The process to generate and download both the private key and the certificate is straightforward using the CloudFlare dashboard. Login as usual and go to the SSL tab for the site for which you want to add the certificate, then select the Origin Server tab within this.
Click the Create Certificate button to start the process. Note that you will be able to copy the certificate afterwards from this screen but the private key that is generated will only be available to copy once. The key is sensitive and should be treated like a password; do not share with anyone or save it unsecured.

You can choose between RSA and ECDSA; note whichever one you select. Make sure that the domains listed cover those on your site and select the validity period. Once you click the next button both the certificate and secret key will be displayed and can be copied to your server. Save in files with extension .pem and .key.
Best practice is to make the key readable only by the root user which should not be generally used to maintain the server. To do so you can run these commands:
sudo chown root:root /path/to/private.key
sudo chmod -R 700 /path/to/private.key
There is an optional step that you can do to add the CloudFlare CA Origin root certificate; search the CloudFlare site for the latest valid certificate, noting that there is a separate one required for RSA and ECDSA, so use the one matching the key that you created.
Download and save the contents to your server and concatenate the contents of your site’s certificate with CloudFlare’s. You can use the following command to do this:
cat /path/to/your-site.pem cloudflare-ecc-root.pem >combined.pem
Now use combined.pem instead of your own certificate in the remaining instructions.
Installing on your server
Take backups of any files you are changing so that you can roll back in case of any problems.
The Ghost blog is served by nginx, and this must be configured to use the certificate. Open the SSL configuration for your site. This can be reached through the linked files in /etc/nginx/sites-enabled/ and will probably be named for your domain. There should be two files, one handling unsecured traffic and another for SSL. Open the latter with a command like:
vi failedtofunction.com-ssl.conf
There should already be a couple of lines defining ssl_certificate and ssl_certificate_key properties. Simply change these to point to the two new files created above. Make sure to end each line with a semicolon.
Restart and Test
Restarting nginx first will give a good idea if your changes have been made correctly. You can test the configuration with sudo /etc/init.d/nginx configtest and restart with sudo /etc/init.d/nginx restart. If there is an error it should output where to look for the problem; fix and then try again or revert to backup.
Once nginx restarts without issues, you can also restart the Ghost blog. Change into the root folder for your site and run ghost restart.
From a browser, connect to the site and check it is still loading correctly.
Full (Strict)
The last step is to go back to the CloudFlare console and turn on Strict (Full). You can do this from the SSL/TLS - Overview tab.
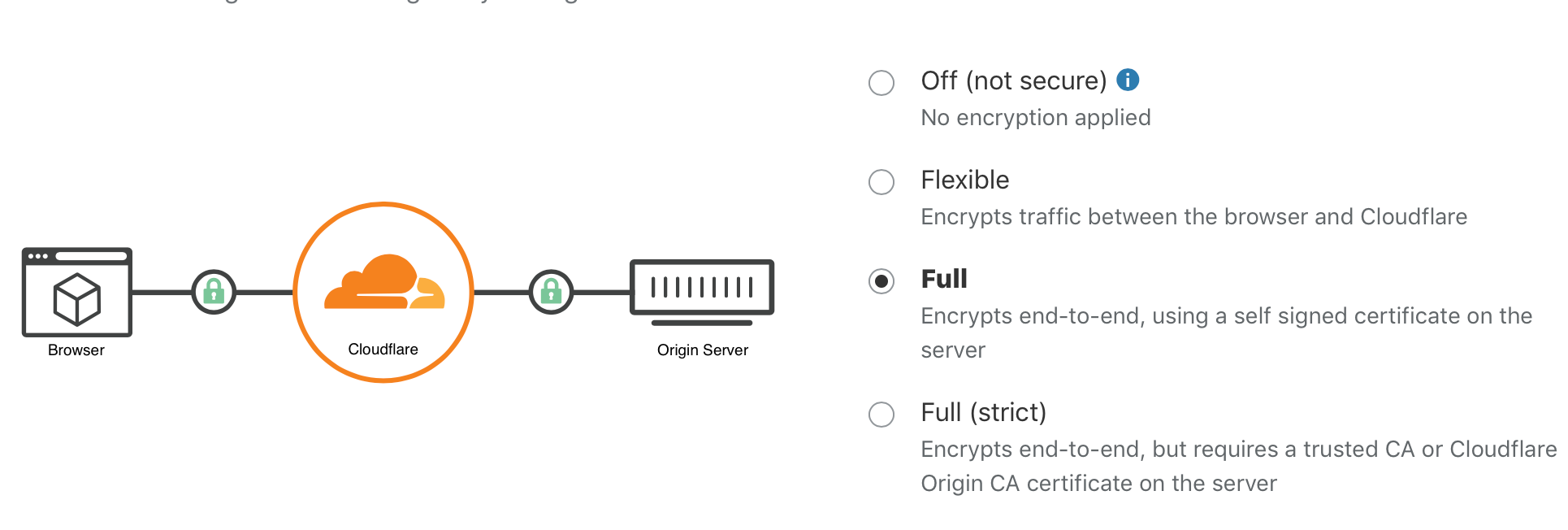
Test using a browser once more and the job is complete.
Further steps might be to clean up your server by removing the Letsencrypt client. There is probably a cron task running on the server to renew the certificate every three months. You can disable this by editing the server’s cron:
sudo crontab -e
Find the line with a reference to LetsEncrypt and either delete the line or place a # character at the start to comment it out so that it does not run.